Data is the lifeblood of any organization, and maintaining its integrity is crucial for smooth operations and decision-making. Database corruption, which can occur due to various reasons such as hardware failures, software bugs, or power outages, can have severe consequences, including data loss, application crashes, and inaccurate reporting. This is where the EF Checksum Manager Crack comes into play, a powerful tool designed to verify data integrity in SQL Server databases.
Understanding Database Corruption
Database corruption refers to the unintended modification, deletion, or alteration of data stored in a database. It can occur at various levels, including the physical storage level (disk corruption), logical level (data structure corruption), or application level (data entry errors). Some common causes of database corruption include:
- Hardware failures: Disk failures, memory errors, or other hardware-related issues can corrupt data.
- Software bugs: Coding errors or bugs in the database management system (DBMS) or applications can lead to corruption.
- Power outages: Unexpected power interruptions during database operations can leave data in an inconsistent state.
- Human errors: Accidental deletion, modification, or mishandling of data by users can result in corruption.
Consequences of database corruption can be severe, ranging from data loss and application crashes to inaccurate reporting and compliance issues. Therefore, it is crucial to have robust mechanisms in place to detect and prevent corruption, which is where the Free download EF Checksum Manager comes into play.
How the Full version crack EF Checksum Manager Works
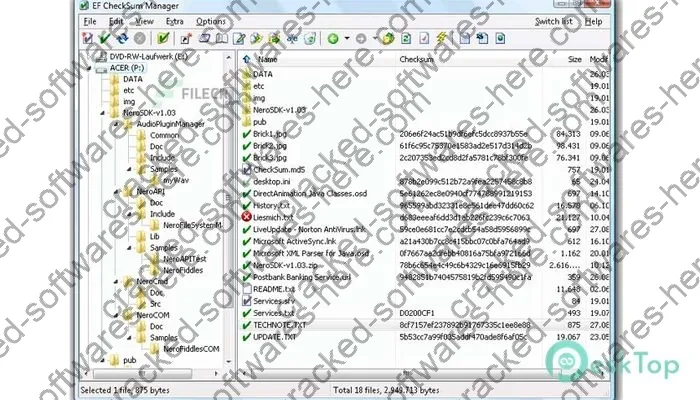
The EF Checksum Manager is a tool that verifies data integrity in SQL Server databases by computing and comparing checksum values for database pages. Here’s how it works:
- Checksum computation: The tool calculates a checksum (hash value) for each database page, which represents the contents of that page.
- Scheduled or manual checks: The checksum operations can be scheduled to run automatically at regular intervals or can be executed manually.
- Comparison and detection: During each run, the tool compares the computed checksums with the previously stored values. Any mismatch indicates potential corruption.
- Alerting and prevention: When corruption is detected, the EF Checksum Manager sends alerts to administrators and prevents auto-recovery mechanisms from attempting to recover the corrupted data, which could further exacerbate the issue.
By regularly running checksum operations, the EF Checksum Manager can identify data corruption early, allowing administrators to take necessary steps to address the issue before it escalates.
See also:
Setting Up the EF Checksum Manager
To set up the EF Checksum Manager, you’ll need to meet the following system requirements:
- SQL Server version: The tool is compatible with SQL Server 2005 and later versions.
- Permissions: The user account running the tool must have appropriate permissions to access the databases and execute DBCC commands.
Here are the steps to download, install, and configure the EF Checksum Manager:
- Download: Download the latest version of the tool from our site.
- Install: Run the installer and follow the prompts to complete the installation.
- Configure: Open the EF Checksum Manager console and navigate to the “Options” tab to configure various settings, such as the schedule for checksum operations, alert preferences (email, pager, etc.), and logging options.
Once installed and configured, the EF Checksum Manager is ready to perform checksum operations on your SQL Server databases.
Running Checksum Operations
The Download free EF Checksum Manager provides two primary methods for running checksum operations: the graphical user interface (GUI) and the command line.
Using the GUI:
- Launch the EF Checksum Manager console.
- Select the desired server and database(s) from the left pane.
- Right-click on the database(s) and choose the appropriate checksum operation (e.g., DBCC CHECKDB, DBCC CHECKCATALOGTUNER, DBCC CHECKCONSTRAINTS, etc.).
- Review the settings and click “Run” to initiate the checksum operation.
Running from the Command Line:
The EF Checksum Manager also provides command-line options for running checksum operations. Here’s an example command:
Msg 824, Level 24, State 2, Line 1
Database 'DatabaseName' has a SINGLE_PAGE corrupted extent (Object ID 1234567, File ID 1, Page 456789). Run DBCC CHECKDB to identify the repair level.
This warning indicates that a single database page within the specified object (table or index) has been corrupted. The report provides the necessary information to identify the affected object and the page ID, allowing administrators to investigate and address the issue.
Resolving Database Corruption
If the Free download EF Checksum Manager detects database corruption, it’s essential to take prompt action to resolve the issue and prevent further data loss or application disruptions. Here are the general steps to follow:
- Identify the extent of corruption: Review the checksum report to understand the specific objects and database pages affected by corruption.
- Stop database activities: If possible, stop all user activities and applications accessing the affected database to prevent further corruption or data modification.
- Attempt repair operations: Depending on the severity and extent of the corruption, you may be able to repair the affected objects using the
DBCC REPAIR_ALLOW_DATA_LOSSorDBCC REPAIR_REBUILDcommands. However, these operations may result in data loss, so proceed with caution and make sure to have recent backups available. - Restore from backups: If the corruption is severe or repair operations are not feasible, your best option may be to restore the affected database from the most recent full backup and then apply any subsequent transaction log backups to minimize data loss.
It’s important to have a robust backup and recovery strategy in place to minimize the impact of database corruption and ensure timely recovery. Additionally, documenting the steps taken to resolve the corruption can aid in identifying and addressing the root cause to prevent future occurrences.
See also:
Best Practices for Using EF Checksum Manager
To maximize the effectiveness of the EF Checksum Manager and ensure proactive data integrity management, consider the following best practices:
- Schedule regular checks: Establish a schedule for running checksum operations based on the size and usage of your databases. For critical databases with high transaction volumes, consider running checks more frequently (e.g., daily or weekly).
- Set up alerts: Configure the EF Checksum Manager to send email or pager alerts to relevant personnel when corruption is detected, enabling prompt action and minimizing potential data loss.
- Create maintenance plans: Incorporate checksum operations into your overall database maintenance plans, ensuring that data integrity checks are performed alongside other routine tasks like backups, index maintenance, and consistency checks.
- Combine with other integrity tools: While the EF Checksum Manager is a powerful tool, consider complementing it with other data integrity solutions, such as backup verification tools or third-party monitoring and auditing solutions.
- Document and analyze incidents: Maintain a detailed log of corruption incidents, the steps taken to resolve them, and any identified root causes. This information can help improve your data integrity processes and prevent similar issues from occurring in the future.
By following these best practices, you can proactively monitor and maintain the integrity of your SQL Server databases, minimizing the risk of data corruption and ensuring the reliability and accuracy of your data.
Conclusion
Data integrity is paramount for any organization relying on databases for critical operations and decision-making. The EF Checksum Manager Crack is a powerful tool that helps ensure data integrity in SQL Server databases by detecting and preventing corruption through regular checksum operations.
By incorporating the EF Checksum Manager into your database maintenance routine and following best practices, you can proactively identify and address corruption issues, minimizing the risk of data loss, application disruptions, and inaccurate reporting. Invest in this tool to safeguard your valuable data and maintain the integrity of your SQL Server databases.
efcmd /sql="DBCC CHECKDB ('DatabaseName')" /srv="ServerName" /log="LogFilePath" /email="EmailAddress"
This command runs the DBCC CHECKDB operation on the specified database, logs the output to the specified file, and sends email notifications to the provided email address.
You can schedule regular checksum operations using Windows Task Scheduler or SQL Server Agent jobs to ensure proactive data integrity checks.
Types of Checksum Operations
The EF Checksum Manager Crack supports various types of checksum operations, each targeting different aspects of the database:
- DBCC CHECKDB: This operation checks the allocation and structural integrity of the entire database, including user and system tables, indexes, and other database objects.
- DBCC CHECKCATALOGTUNER: This operation verifies the integrity of the system metadata stored in the system tables of the database.
- DBCC CHECKCONSTRAINTS: This operation checks for constraint violations, such as referential integrity issues, in the database.
- DBCC CHECKFILEGROUP: This operation checks the integrity of a specific filegroup within the database.
- DBCC CHECKTABLE: This operation checks the integrity of a specific table or set of tables within the database.
Depending on your requirements and the size of your database, you may choose to run specific checksum operations or a combination of them.
Reading Checksum Reports
After running a checksum operation, the EF Checksum Manager generates a detailed report that provides information about the operation’s status and any detected issues. The report layout typically includes the following sections:
- Summary: This section provides an overview of the checksum operation, including the start and end times, the database(s) checked, and the overall status (success or failure).
- Errors and Warnings: If any errors or warnings were encountered during the checksum operation, they will be listed in this section, along with their severity levels and descriptions.
- Object Details: This section provides detailed information about the objects checked during the operation, such as tables, indexes, and constraints, including their names, sizes, and any issues detected.
- Corruption Details: If any corruption was detected, this section will provide detailed information about the affected database pages, including the page IDs, the type of corruption, and the potential cause (if known).
Here’s an example of a common corruption warning that might appear in the report:
Msg 824, Level 24, State 2, Line 1
Database 'DatabaseName' has a SINGLE_PAGE corrupted extent (Object ID 1234567, File ID 1, Page 456789). Run DBCC CHECKDB to identify the repair level.
This warning indicates that a single database page within the specified object (table or index) has been corrupted. The report provides the necessary information to identify the affected object and the page ID, allowing administrators to investigate and address the issue.
Resolving Database Corruption
If the Free download EF Checksum Manager detects database corruption, it’s essential to take prompt action to resolve the issue and prevent further data loss or application disruptions. Here are the general steps to follow:
- Identify the extent of corruption: Review the checksum report to understand the specific objects and database pages affected by corruption.
- Stop database activities: If possible, stop all user activities and applications accessing the affected database to prevent further corruption or data modification.
- Attempt repair operations: Depending on the severity and extent of the corruption, you may be able to repair the affected objects using the
DBCC REPAIR_ALLOW_DATA_LOSSorDBCC REPAIR_REBUILDcommands. However, these operations may result in data loss, so proceed with caution and make sure to have recent backups available. - Restore from backups: If the corruption is severe or repair operations are not feasible, your best option may be to restore the affected database from the most recent full backup and then apply any subsequent transaction log backups to minimize data loss.
It’s important to have a robust backup and recovery strategy in place to minimize the impact of database corruption and ensure timely recovery. Additionally, documenting the steps taken to resolve the corruption can aid in identifying and addressing the root cause to prevent future occurrences.
See also:
Best Practices for Using EF Checksum Manager
To maximize the effectiveness of the EF Checksum Manager and ensure proactive data integrity management, consider the following best practices:
- Schedule regular checks: Establish a schedule for running checksum operations based on the size and usage of your databases. For critical databases with high transaction volumes, consider running checks more frequently (e.g., daily or weekly).
- Set up alerts: Configure the EF Checksum Manager to send email or pager alerts to relevant personnel when corruption is detected, enabling prompt action and minimizing potential data loss.
- Create maintenance plans: Incorporate checksum operations into your overall database maintenance plans, ensuring that data integrity checks are performed alongside other routine tasks like backups, index maintenance, and consistency checks.
- Combine with other integrity tools: While the EF Checksum Manager is a powerful tool, consider complementing it with other data integrity solutions, such as backup verification tools or third-party monitoring and auditing solutions.
- Document and analyze incidents: Maintain a detailed log of corruption incidents, the steps taken to resolve them, and any identified root causes. This information can help improve your data integrity processes and prevent similar issues from occurring in the future.
By following these best practices, you can proactively monitor and maintain the integrity of your SQL Server databases, minimizing the risk of data corruption and ensuring the reliability and accuracy of your data.
Conclusion
Data integrity is paramount for any organization relying on databases for critical operations and decision-making. The EF Checksum Manager Crack is a powerful tool that helps ensure data integrity in SQL Server databases by detecting and preventing corruption through regular checksum operations.
By incorporating the EF Checksum Manager into your database maintenance routine and following best practices, you can proactively identify and address corruption issues, minimizing the risk of data loss, application disruptions, and inaccurate reporting. Invest in this tool to safeguard your valuable data and maintain the integrity of your SQL Server databases.

This platform is absolutely impressive.
It’s now a lot more user-friendly to do jobs and track information.
The loading times is a lot faster compared to older versions.
I absolutely enjoy the new layout.
I would strongly suggest this tool to anyone looking for a powerful solution.
I appreciate the improved dashboard.
I would absolutely endorse this tool to anyone looking for a robust platform.
The speed is a lot enhanced compared to last year’s release.
The performance is significantly better compared to the previous update.
I love the enhanced dashboard.
It’s now much more intuitive to do tasks and manage content.
The recent features in release the newest are incredibly great.
The recent enhancements in version the latest are incredibly helpful.
The loading times is significantly faster compared to older versions.
The latest features in release the latest are so helpful.
This platform is truly great.
This program is definitely awesome.
The new enhancements in update the latest are really awesome.
The loading times is a lot improved compared to older versions.
It’s now far simpler to finish projects and manage information.
I love the new dashboard.
I really like the new dashboard.
The loading times is significantly improved compared to older versions.
The loading times is so much enhanced compared to older versions.
The speed is significantly faster compared to the previous update.
It’s now a lot simpler to get done work and track information.
I would strongly recommend this software to professionals needing a top-tier product.
I really like the enhanced dashboard.
The speed is so much enhanced compared to older versions.
The latest enhancements in release the latest are incredibly useful.
The latest enhancements in version the newest are so cool.
It’s now much more intuitive to get done tasks and manage data.
It’s now far more user-friendly to complete jobs and track content.
The latest capabilities in version the newest are incredibly helpful.
The program is truly great.
This platform is absolutely awesome.
This application is absolutely great.
It’s now a lot more intuitive to complete jobs and track data.
I would strongly endorse this application to anybody needing a top-tier product.
The program is definitely fantastic.
The recent enhancements in version the latest are really great.
I appreciate the upgraded dashboard.
It’s now much easier to get done tasks and track content.
This software is truly impressive.
The loading times is significantly faster compared to last year’s release.
The new functionalities in release the newest are so helpful.
The new features in update the latest are really great.
The performance is significantly enhanced compared to the original.
The loading times is a lot improved compared to the previous update.
It’s now much simpler to do tasks and track data.
The new updates in release the latest are so cool.
It’s now much simpler to do tasks and organize data.
I would absolutely endorse this application to anybody looking for a powerful solution.
It’s now far more intuitive to do tasks and track data.
The performance is significantly improved compared to older versions.
I absolutely enjoy the improved dashboard.
It’s now a lot simpler to finish tasks and track content.
I absolutely enjoy the upgraded workflow.
I love the upgraded interface.
I really like the improved interface.
The performance is a lot enhanced compared to last year’s release.
I appreciate the upgraded dashboard.
I would definitely suggest this program to anybody needing a top-tier solution.
The tool is definitely great.
The latest features in version the newest are really helpful.
The recent features in release the latest are extremely useful.
I absolutely enjoy the improved interface.
The recent capabilities in release the latest are incredibly awesome.
The platform is definitely fantastic.
The recent enhancements in update the newest are so helpful.
The recent enhancements in update the latest are so helpful.
The loading times is significantly enhanced compared to the original.
It’s now far more intuitive to complete tasks and track information.
The speed is so much better compared to the previous update.
This program is absolutely fantastic.
It’s now a lot easier to do work and manage data.
It’s now far more user-friendly to get done tasks and manage data.
The new capabilities in version the newest are incredibly awesome.
I would strongly endorse this application to professionals looking for a powerful product.
The tool is absolutely impressive.
The loading times is a lot enhanced compared to the original.
I really like the improved layout.
It’s now far more intuitive to do jobs and manage information.
The software is truly awesome.
The performance is significantly better compared to older versions.
I would absolutely recommend this application to professionals needing a robust platform.
The speed is so much better compared to the previous update.
The responsiveness is a lot enhanced compared to older versions.
It’s now much simpler to do projects and manage data.
This program is absolutely awesome.
I would absolutely endorse this program to professionals needing a high-quality platform.
The new capabilities in version the newest are incredibly useful.
The loading times is significantly enhanced compared to the previous update.
The tool is really impressive.
I would strongly recommend this tool to anyone wanting a high-quality product.
I would definitely suggest this program to anybody wanting a robust solution.
I would strongly recommend this tool to anyone needing a top-tier platform.
I would strongly suggest this program to anybody needing a high-quality product.
The loading times is so much better compared to last year’s release.
The recent updates in update the newest are so helpful.
The loading times is a lot improved compared to older versions.